This article demonstrates how to enable Single Sign-on (SSO) for GMO Sign using AzureAD. GMO Sign can be integrated with other SSO services like okta, trustlogin, cloudgate, gluegent, skuid, onelogin, etc.
|
Prerequisites:
|
Summary of the steps :
- Create AzureAD Enterprise application, and input setup information of GMO Sign.
- Acquire IDP Entity ID/ SSO-URL/ Certificate from the application you created in Step 1.
- Change the user attribute of the application you created in Step 1 to the user's email address (user.email).
- Pass the IDP Entity ID/ SSO-URL/ Certificate you acquired in Step 2 to the contact person of GMO Sign and setup notification.
- Assign the user to the application you created in Step 1.
- Confirm communication via Test feature of Single sign-on.
Setup in Azure
(1) Click Sign in on the Microsoft Azure Home page
(2) Sign in with Azure log in ID and Password
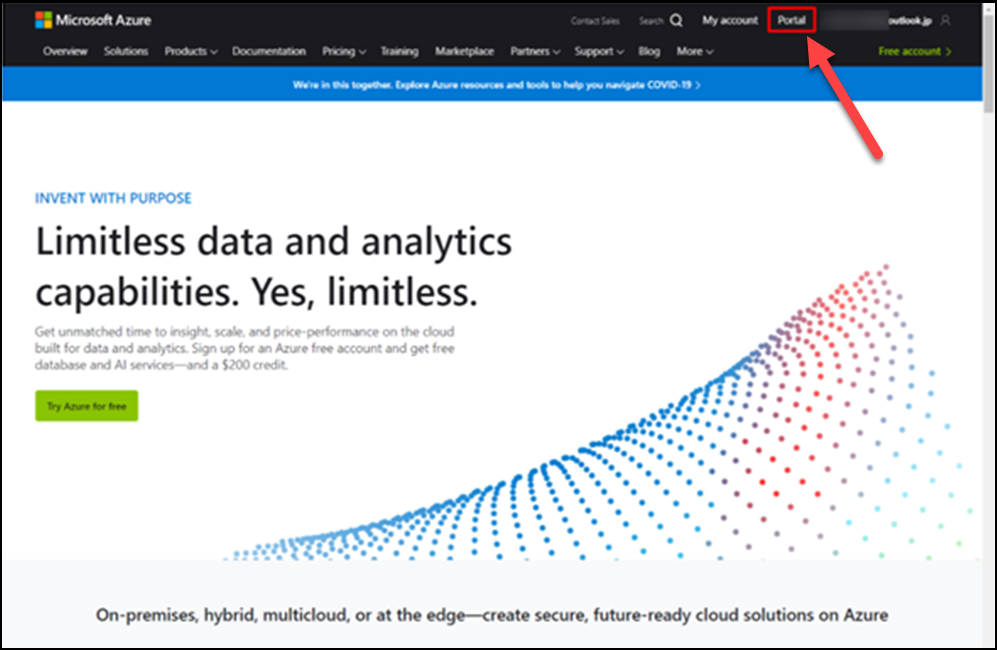
(3) After signing in, click Portal.
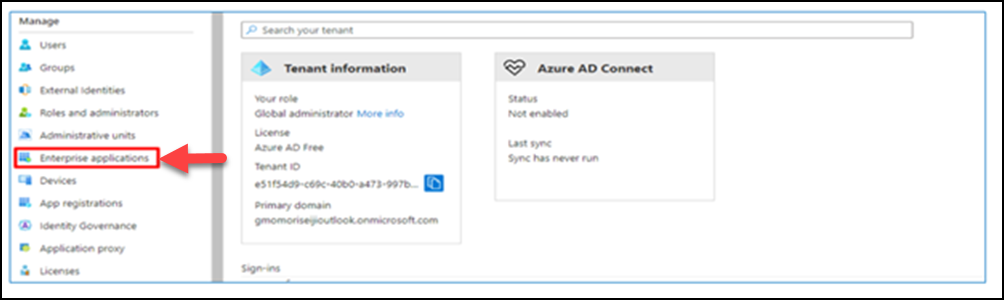
(4) Click Azure Active Directory.

(5) Click Enterprise Application.
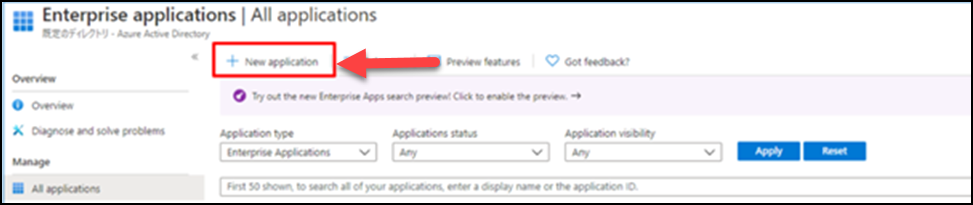
(6) Click New application.
(7) Click Create your own application.
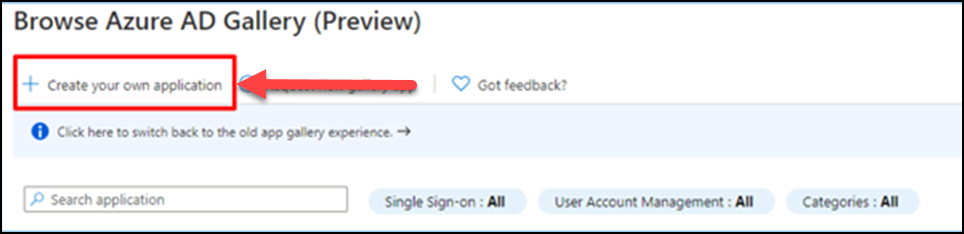
Enter the application name and create.
(It takes a couple of minutes to update after pressing Create.)
(8) Once you see the confirmation message, click Set up single sign-on.
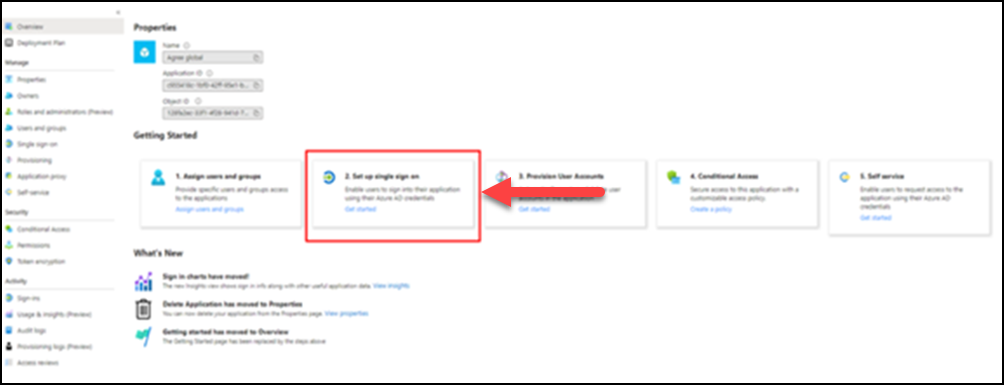
Select SAML for a single sign-on method.
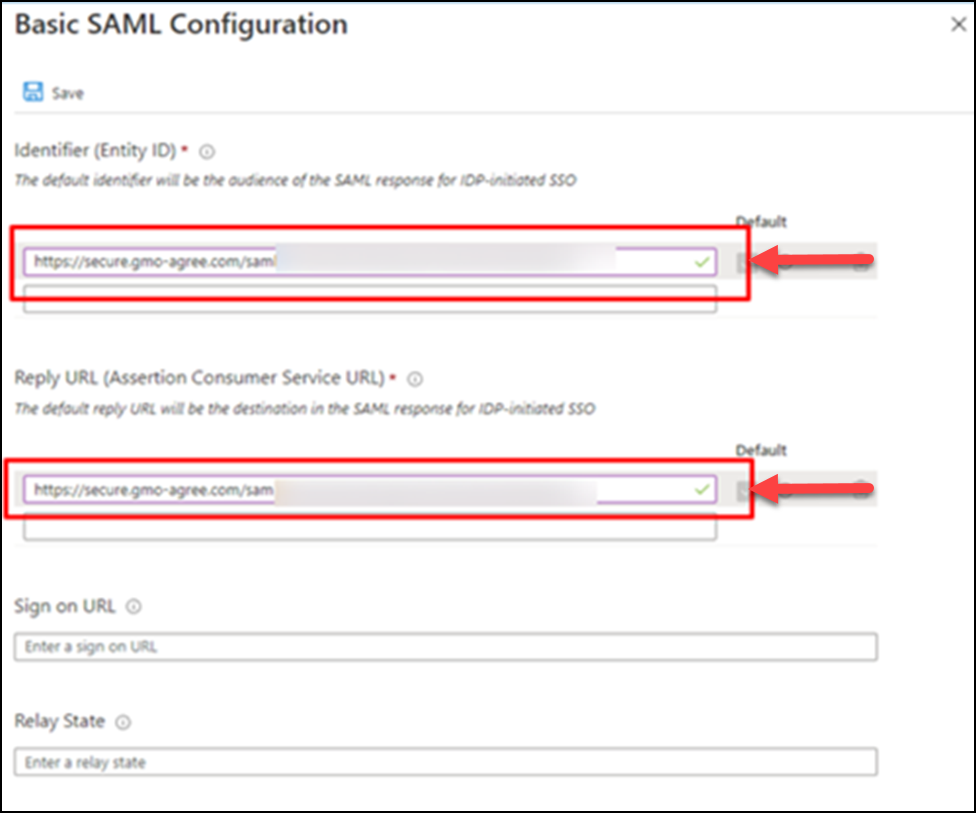
(9) Click Edit under Basic SAML Configuration.
(10) Enter identifier (Entity ID) and Reply URL (Assertion Consumer Service URL) and Save.
(Provided by GMO Sign representative)
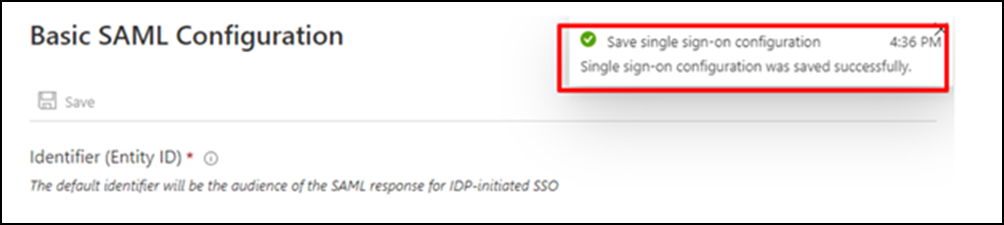
(11) The below message will appear when you save it successfully.
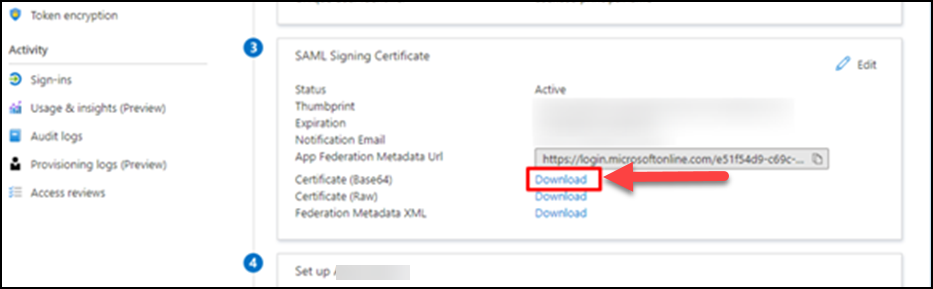
Acquire IDP Entity ID/ SSO-URL/ Certificate
(12) Download the certificate (Base64). A file named as “application name.cer” will be downloaded.
※Please attach this file to an email and send it to your GMO Sign Representative.
Share IDP Entity ID/ SSO-URL/ Certificate with GMO Sign Representative
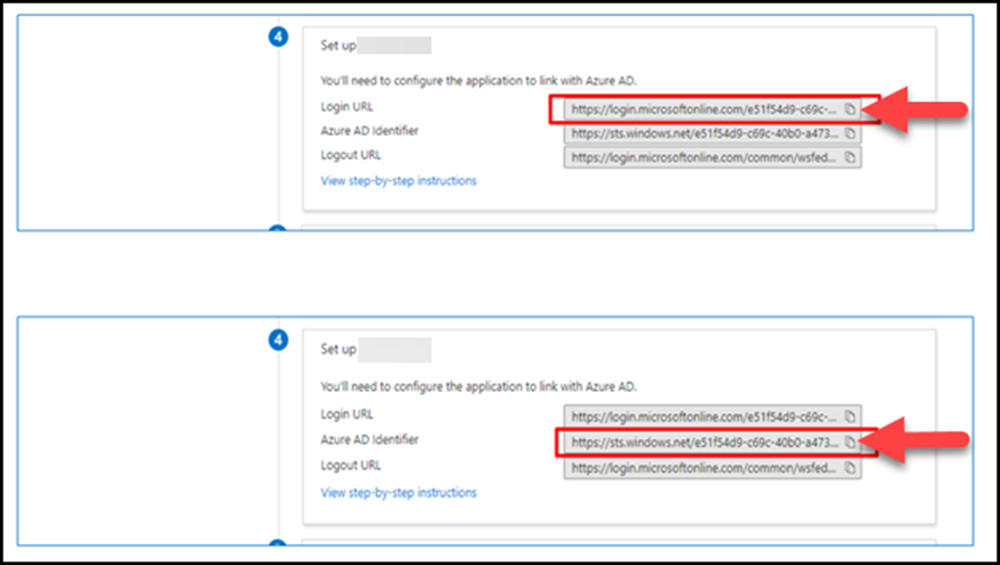
(13) Copy login URL information and AzureAD identifier information and paste them to notepad and share it with the GMO Sign representative.
Change user attribute to user's email address (user.email)
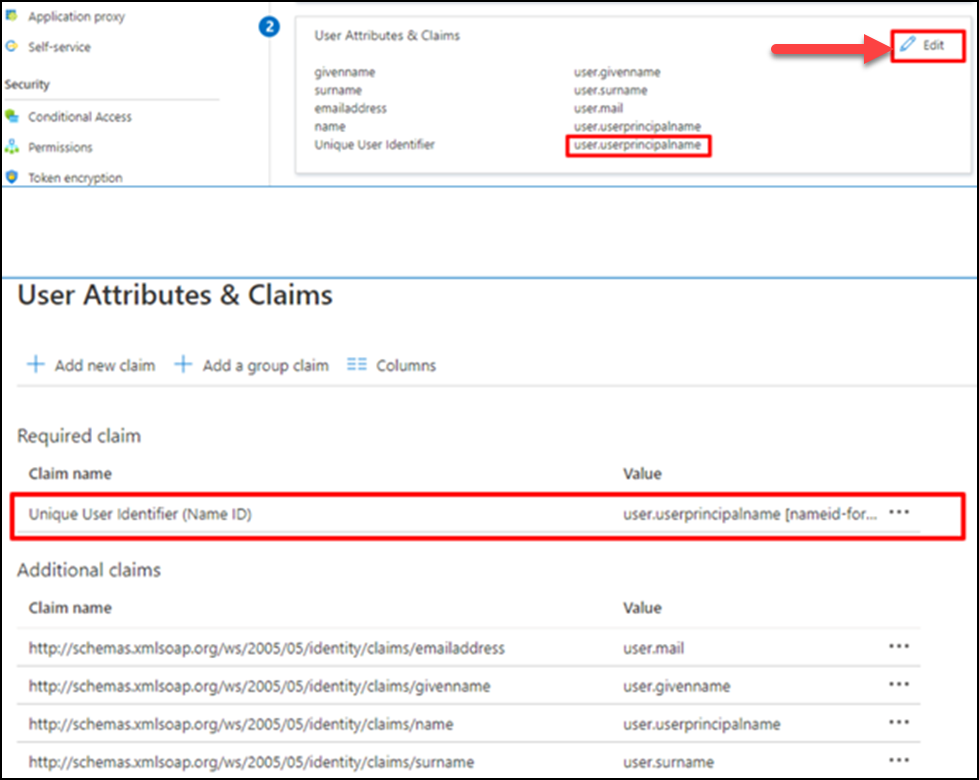
(14) Change the user ID in User Attributes to an email address. Click Edit under User Attributes & Claims. Next, click Unique User Identifier.
※Soon after the app is created, it is set to "user.userprincipalname", and in this state, GMO Sign's SAML integration will not work.
(15) Select Source as attribute and change it to "user.mail", and Save.
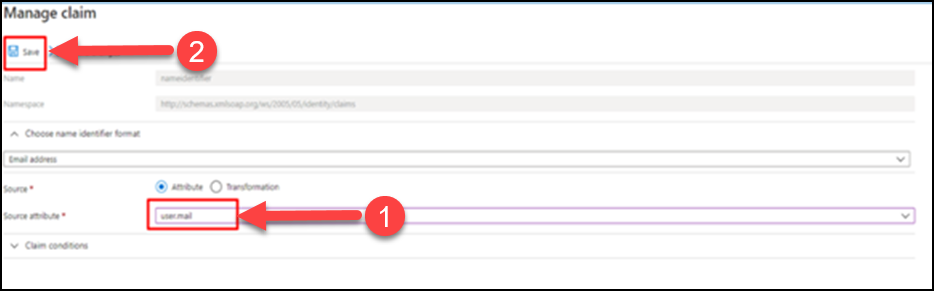
(16) The changes will be saved.
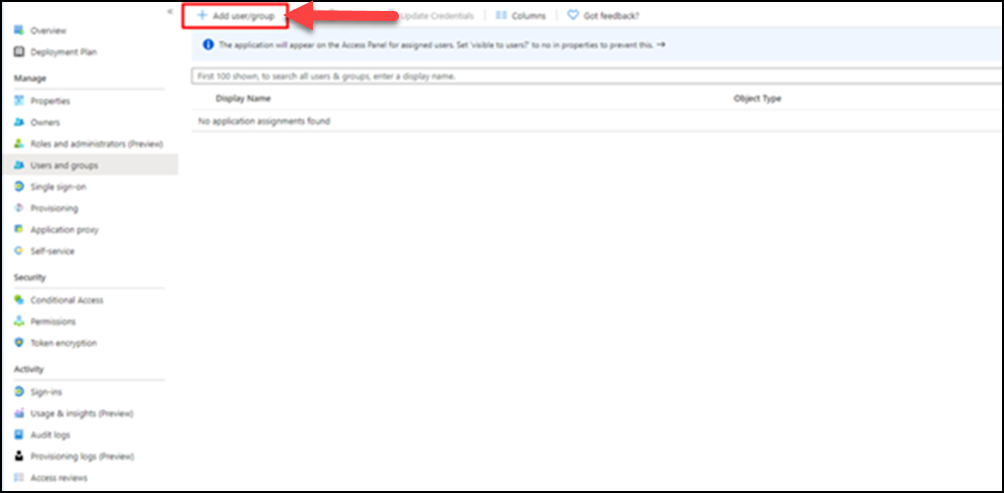
User Registration
(17) Register users via Add user.
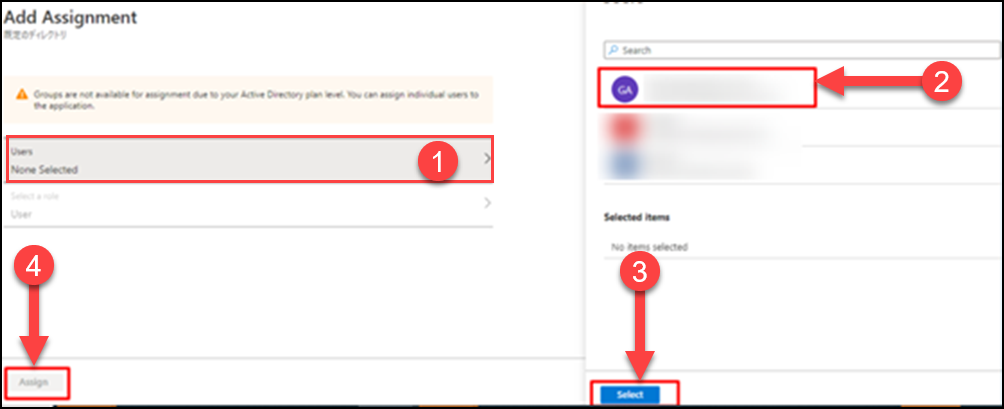
(18) Click Users and select a user (who is already registered) from the displayed list. Click on Select >> Assign.
(19) The assigned user(s) will be listed on your screen if successfully registered.
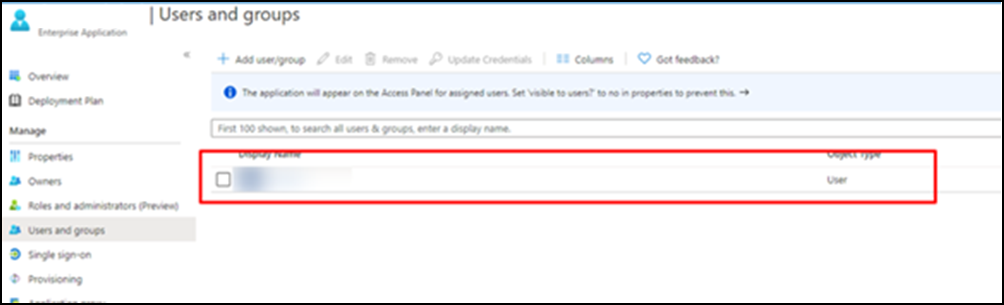
(Azure AD settings are completed.)
Single Sign-On Communication Confirmation
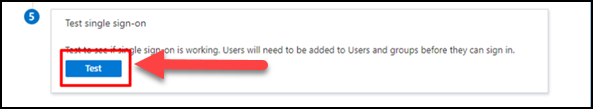
(20) Go to 'Test single sign-on' section and click on Test.
(21) Select Sign in as current user.
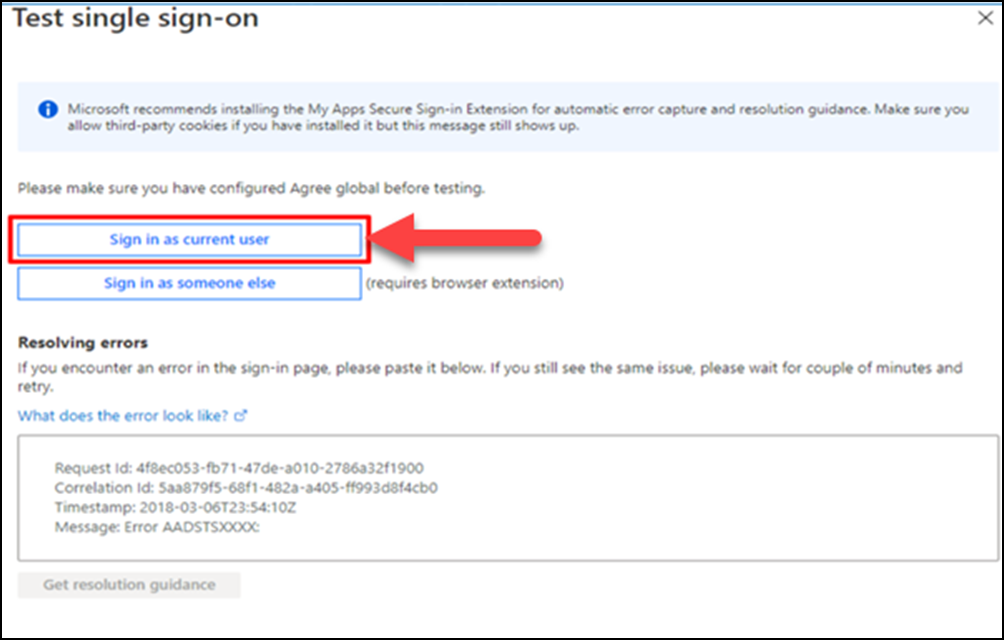
※ You can confirm the communication if users exist in GMO Sign as well.
(22) If the configuration was successfully setup, you will be directed to the GMO Sign dashboard screen.